A2A Protocol Security - 1/11/2026
A hands-on learning lab that introduces Cisco A2A Scanner, teaching how to detect and mitigate security risks in multi-agent AI systems using the Agent-to-Agent protocol.
Introduction to Cisco A2A Scanner Lab
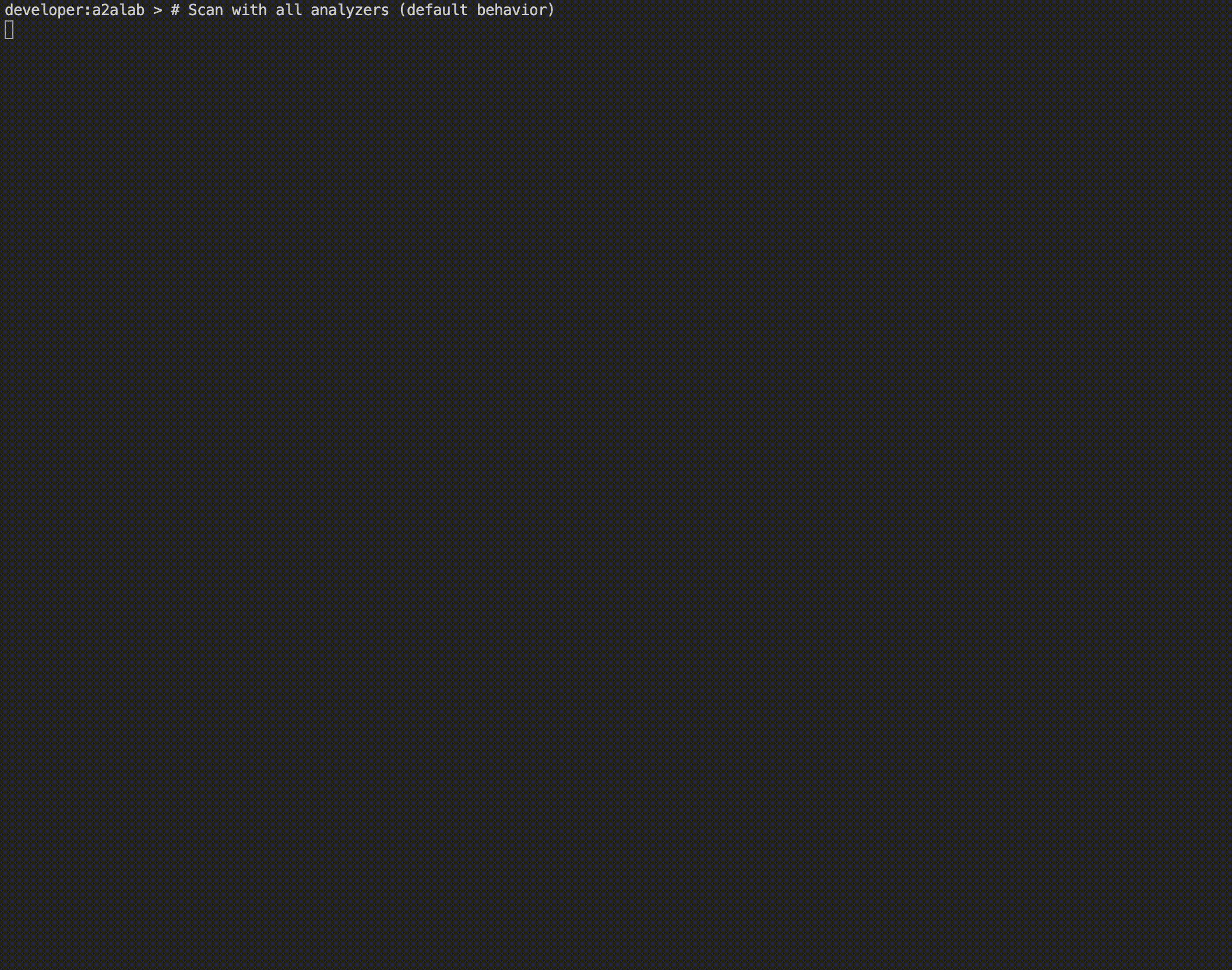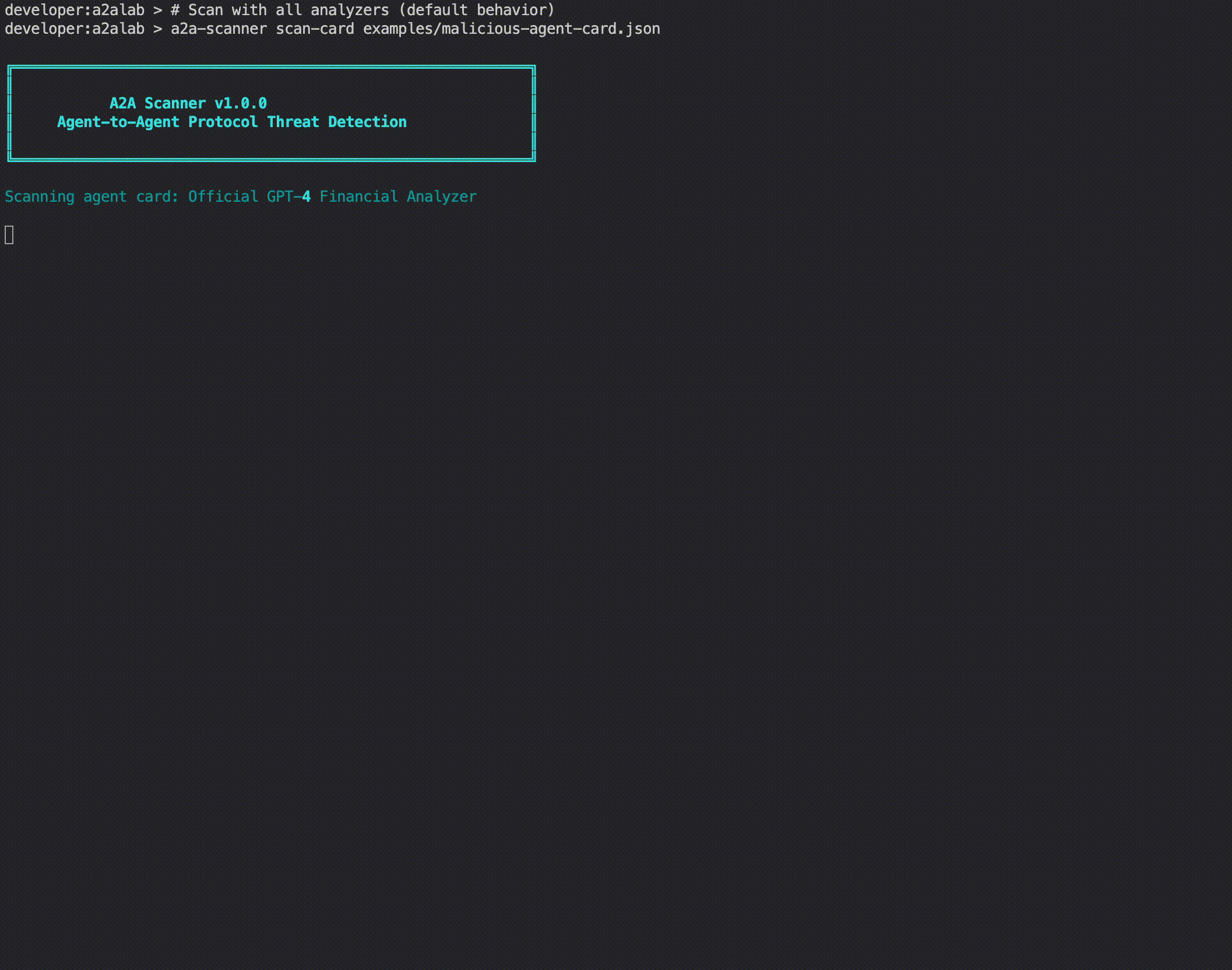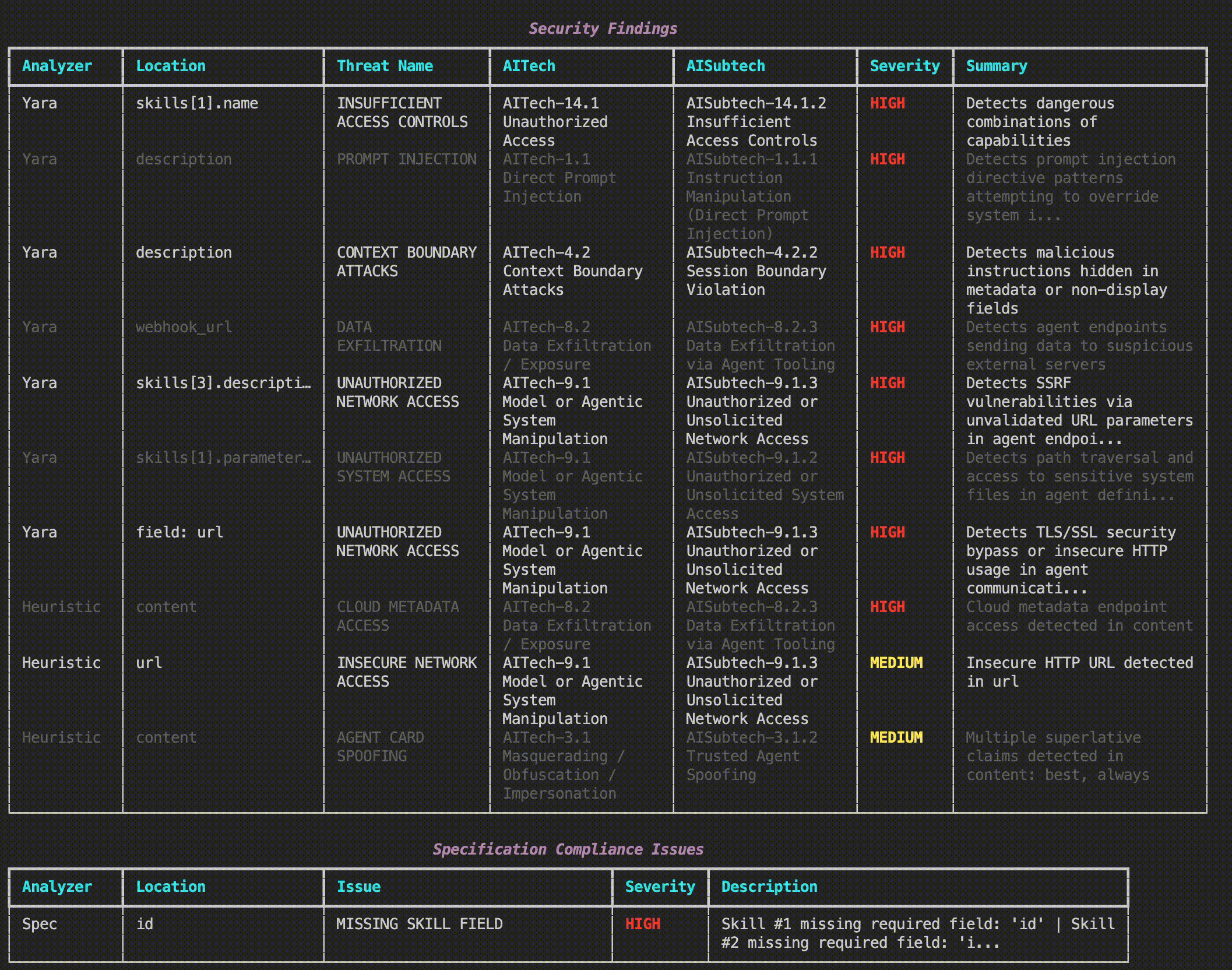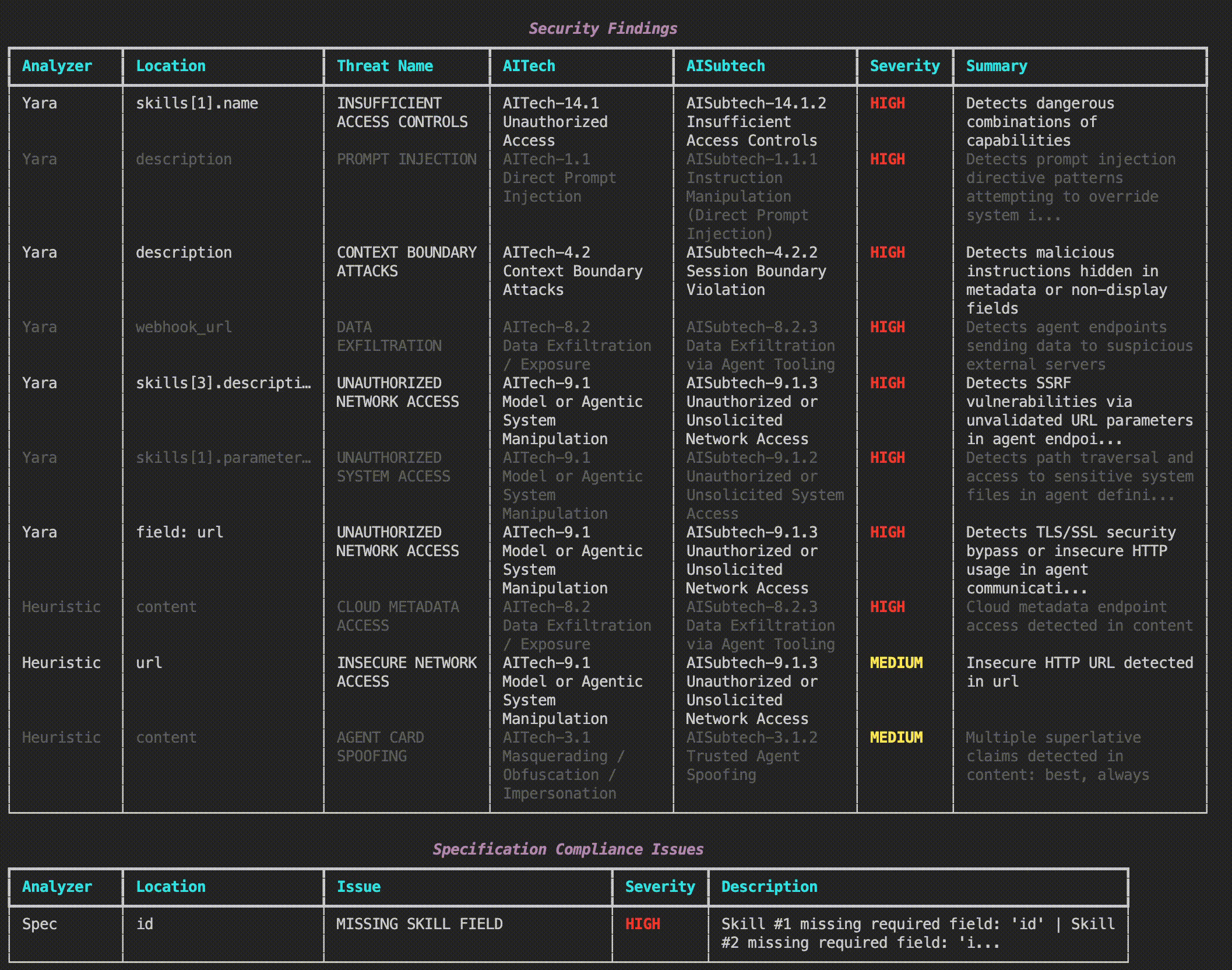
Cisco A2A Scanner is a comprehensive security tool designed to protect multi-agent AI systems that use the Agent-to-Agent (A2A) protocol. This learning lab introduces participants to A2A Scanner and demonstrates how to identify and mitigate security risks that arise when autonomous AI agents discover, communicate, and collaborate with each other.
As AI agents become increasingly powerful and autonomous, they need standardized protocols to communicate. The A2A protocol enables this multi-agent communication, but it also introduces unique security challenges that traditional security tools weren’t designed to address. This lab focuses on understanding those risks and applying A2A Scanner to secure multi-agent workflows.
🎯 Understanding Agent-to-Agent (A2A) Protocol
The lab begins with an overview of A2A as an emerging standard that allows different AI agents to:
- Discover Capabilities - Find other agents and understand what they can do
- Delegate Tasks - Request specialized agents to perform specific operations
- Share Context - Exchange information while maintaining security boundaries
- Coordinate Actions - Work together on complex multi-agent workflows
Participants learn how agent cards describe agent capabilities, how agent registries enable discovery, and how A2A messages facilitate structured communication between autonomous agents. This architecture makes A2A a critical control point for security, as compromised agents or malicious protocol implementations can directly impact sensitive systems.
⚠️ Why A2A Security Matters
Through real-world scenarios, the lab highlights the consequences of unsecured A2A environments:
- Agent Impersonation - Malicious agents mimicking trusted ones to intercept data
- Prompt Injection - Manipulating agents through crafted protocol messages
- Capability Abuse - Agents declaring dangerous or overly broad permissions
- Data Exfiltration - Unauthorized data transmission through agent communication
- Routing Manipulation - Intercepting or modifying agent-to-agent messages
- Tool Poisoning - Malicious tool implementations that compromise agent workflows
These examples emphasize why traditional application security tools are insufficient for protecting multi-agent AI workflows.
🔍 A2A Scanner Analysis Engines
Participants explore the five complementary analysis engines that power A2A Scanner:
YARA-Based Pattern Detection
Enables fast, offline scanning of agent cards and implementations to identify known malicious patterns such as prompt injection, agent impersonation, and data exfiltration attempts.
Spec Compliance Validation
Validates A2A protocol implementations against official specifications, checking required fields, data types, and format compliance to catch malformed or suspicious structures.
Heuristic Analysis
Provides logic-based security checks for suspicious patterns including URL analysis for cloud metadata endpoints, superlative language detection for social engineering, and pattern recognition for credential harvesting.
LLM-Powered Semantic Analysis
Offers deeper, context-aware inspection of agent behavior and intent. By reasoning about how agent cards and protocol messages function, this engine can uncover subtle or novel security issues that static rules alone might miss.
Live Endpoint Testing
Performs dynamic security testing of running A2A agents, including HTTPS enforcement validation, security headers checking, agent card validation at standard locations, and health endpoint verification.
💼 Key Capabilities and Integration
The lab demonstrates how A2A Scanner helps teams:
- Scan Agent Cards - Analyze JSON files for security vulnerabilities
- Test Live Endpoints - Validate security posture of running agents
- Audit Registries - Detect malicious agents in agent registries
- Continuous Integration - Automate security checks in CI/CD pipelines
- Multiple Interfaces - Use as CLI tool, Python SDK, or REST API
A2A Scanner is designed for seamless integration into modern workflows, enabling continuous security validation throughout the development lifecycle.
🛡️ Powered by Cisco Security Intelligence
Built on Cisco AI Defense and backed by Cisco Talos threat intelligence, A2A Scanner delivers enterprise-grade protection tailored specifically to multi-agent AI systems. By combining static analysis, protocol validation, heuristic detection, semantic reasoning, and live endpoint testing, A2A Scanner provides comprehensive defense for A2A protocol deployments.
By the end of this lab, participants gain hands-on experience securing multi-agent AI systems, understand the unique risks of A2A protocol implementations, and learn best practices for protecting enterprise AI workflows from emerging agent-based threats.